Sophos Firewall v20 is now available
New innovations and top-requested features
We are extremely pleased to announce that Sophos Firewall v20 is now available with an innovative new active threat response capability, several networking enhancements, added support for securing your remote workforce, and many of your top-requested features.
Sophos Firewall v20 is a free upgrade for all licensed Sophos Firewall customers.
Watch the video below for an overview of what’s new, download the What’s New PDF, or read on for the full details and deep-dive demo videos.
Active Threat Response:
- Extending Synchronized Security to MDR and XDR provides a direct feed for security analysts to share active threat information with the firewall to enable it to automatically respond to active threats without creating any firewall rules.
- Dynamic Threat Feeds introduces a new threat feed API framework that is easily extensible. It enables threat intelligence to be shared by the Sophos X-Ops team, other Sophos products like MDR and XDR, and ultimately 3rd party threat feeds in the future.
- Synchronized Security now extends the same Red Heartbeat, automated response that Sophos Firewall has always had, to MDR/XDR identified threats, to ensure compromised hosts are not able to move laterally or communicate out while details including host, user, and process are readily available for follow-up. Synchronized Security has also been enhanced with added scalability and reduced false missing heartbeats for devices that are in a sleep or hibernate state.
![]()
Watch the Active Threat Response demo video.
Remote Worker Protection and SASE:
- ZTNA Gateway Integration makes ZTNA deployments even easier by integrating a ZTNA gateway directly into the firewall. This means any organization that needs to provide remote access to applications hosted behind the firewall, doesn’t need to deploy a separate gateway on a VM – they can simply take advantage of the gateway integrated into their firewall. When combined with our single-agent deployment on the remote device, ZTNA couldn’t possibly get any easier – it’s literally zero-touch zero-trust.
![]()
- 3rd Party SD-WAN Integration makes it easy to onramp SD-WAN traffic onto Cloudflare, Akami, or Azure backbone networks to take advantage of their enormous infrastructure, reach, and networking and security services.
- Sophos DNS Protection is our new cloud-delivered web security service that will be available separately in early access very soon. It provides a new Sophos hosted domain name resolution service (DNS) with compliance and security features that are fully supported by Sophos Firewall. This service provides an added layer of web protection, preventing access to known compromised or malicious domains across all ports, protocols, or applications – both unencrypted and encrypted. More news on this new service coming soon.
Network Scalability and Resiliency Enhancements:
- New VPN Portal provides a new containerized, hardened self-service portal for end users to download VPN clients and configuration, auto-provisioning, and clientless VPN bookmarks.
![]()
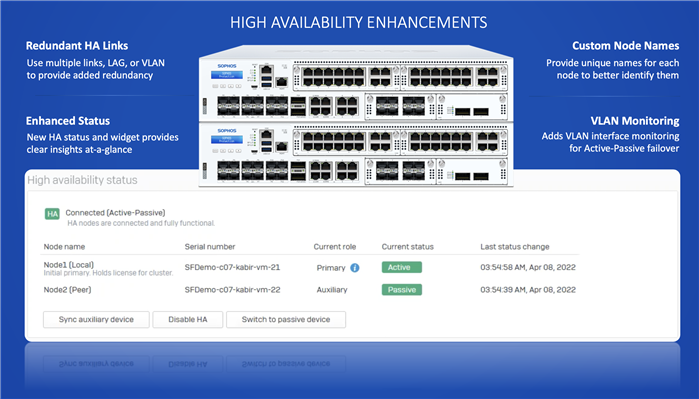
- IPsec Enhancements include seamless HA failover, tunnel status monitoring via SNMP, unique PSK support for the same local and remote gateway connections, and DH Group 27-30 / RFC6954 support.
- SSL VPN Enhancements include FQDN (fully qualified domain name) host and group support for both remote access and site-to-site SSL VPN.
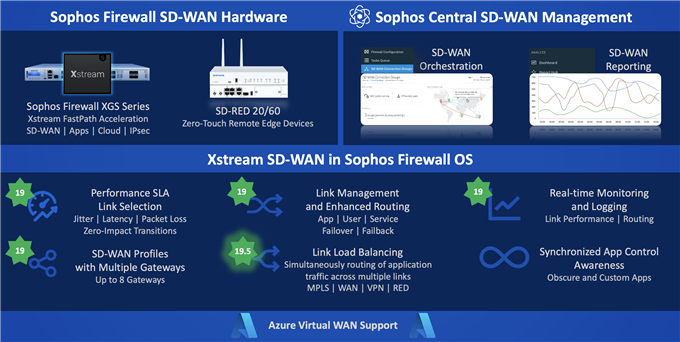
- SD-WAN Scalability increases SD-WAN gateway scalability by 3x to 3072 gateways and the number of SD-WAN profiles to 1024.
- IPv6 Enhancements include DHCP Prefix Delegation to seamlessly integrate with your ISP and new enhancements to the dynamic routing engine now support BGPv6 for improved IPv6 interoperability.
Watch a video overview of the VPN Enhancements or the IPv6 BGPv6 and DHCP Prefix Delegation capabilities.
Streamlined Management:
- Interface Enable/Disable delivers a top-requested feature to easily disable or enable network interfaces on the firewall without losing any configuration.
- Object Reference Lookup addresses another top-requested feature to find where a given host or service object is used in rules, policies, and routing.
- Hi-Res Display Support adds increased horizontal scalability to the management console to take advantage of high-resolution displays to reduce horizontal scrolling.
- Auto-rollback on Failed Firmware Updates reduces any disruption, including high-availability deployments.
- Backup and Restore now includes the option to restore a backup from a firewall with integrated Wi-Fi to a firewall without Wi-Fi.
- Azure AD SSO for Captive Portal adds support for user authentication on the captive portal using their Azure AD credentials.
- Azure Group Import and RBAC add support for a new import assistant for Azure AD groups and automatic promotion for role-based admin changes.
Watch videos covering the new Management features and Quality of Life Enhancements and Azure AD capabilities
Other Enhancements
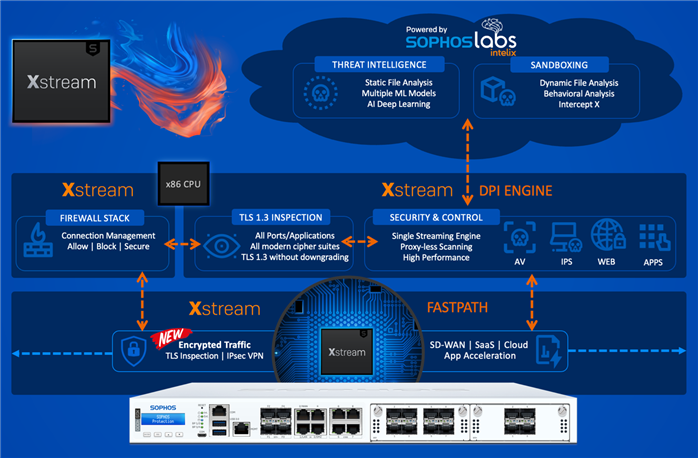
- Web Application Firewall (WAF) Enhancements include geo IP policy enforcement, custom cipher configuration, and TLS version settings, as well as improved security with HSTS enforcement as well as X-Content-Type-Options enforcement.
- Azure Single Arm Deployment Support enables the choice of a smaller instance size to save on infrastructure costs and reduce network and operational complexity.
Get More Details on What’s New
Download the full What’s New guide for a complete overview of all the great new features and enhancements in v20.
Check out the v20.0 GA release notes for more details including the known issues list. Full Product Documentation is available online and within the product.
Watch the Demo Video Series:
How to Get v20
As with every firewall release, Sophos Firewall v20 is a free upgrade for all licensed Sophos Firewall customers and should be applied to all supported firewall devices as soon as possible. This release not only contains great features and performance enhancements, but also important security fixes.
This firmware release will follow our standard update process.
The new v20 firmware will be gradually rolled out to all connected devices over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available, allowing you to schedule the update at your convenience.
Sophos Firewall v20 is a fully supported upgrade from any supported Sophos Firewall firmware version.
Firmware downloads – Now from Sophos Central
Please note that Sophos Firewall firmware updates are now downloaded from Sophos Central. Get the full details here or follow this quick guide (below) to get the latest v20 firmware for your firewall:
- Login to your Sophos Central account and select “Licensing” from the drop-down menu under your account name in the top right of the Sophos Central console…
![]()
- Select Firewall Licenses on the top left of this screen…
![]()
- Expand the firewall device you’re interested in updating by clicking the “>” to show the licenses and firmware updates available for that device…
![]()
- Click the firmware release you want to download (note there is currently an issue with downloads working in Safari so please use a different browser such as Chrome).
- You can also click “Other downloads” in this same box above to access initial installers and software platform firmware updates.



 (SFOS 19.5 is in early access at the moment)
(SFOS 19.5 is in early access at the moment)