To migrate fileshares into Microsoft 365 / OneDrive / Sharepoint, this tool come in handy.
It is not to be compared with the SharePoint Migration Tool, as it can only migrate fileshares, as the opposite can do both.
So we have this file share that we need moved to a SharePoint document library:
How does it work?
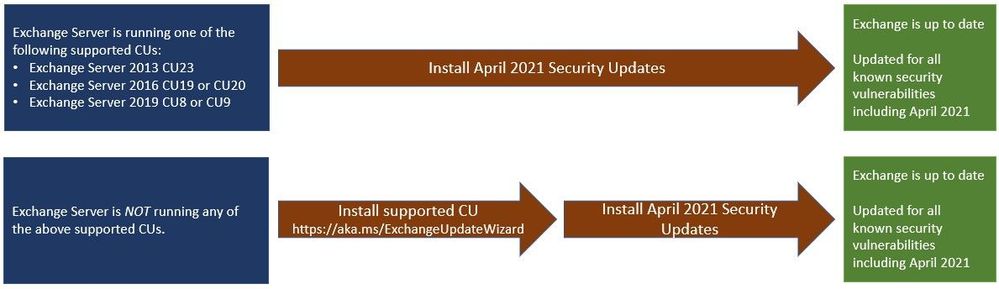
It works in three simple steps:

- Setup migration agents. Download and install a setup file on each computer or virtual machine you want to connect to Migration Manager.
- Create tasks & migrate. Create a task by entering the URL of the network file share that you want to migrate (your source) and the URL of the SharePoint site where you are migrating your content (your destination). Migration Manager does the rest. However many tasks you create, Migration Manager will automatically distribute the tasks across all the connected agents.
- Monitor and report. Monitor progress across all agents and access reports from one central location.
Go ahead and log into Migration Manager page of the new SharePoint admin center

Download the agent setup file and put it on the file server hosting the share, it will be used for a migration agent and you can install multiple of them, if yourenvironment needs it.
Run the file on the file server:

Remember the permissions and press next:

Fill in SharePoint admin on first prompt and domain admin on the next, press “Install”:

Do a test and press close:

Now head back to SharePoint Migration page, and your agent should show as ONLINE:

So we are go to GO!
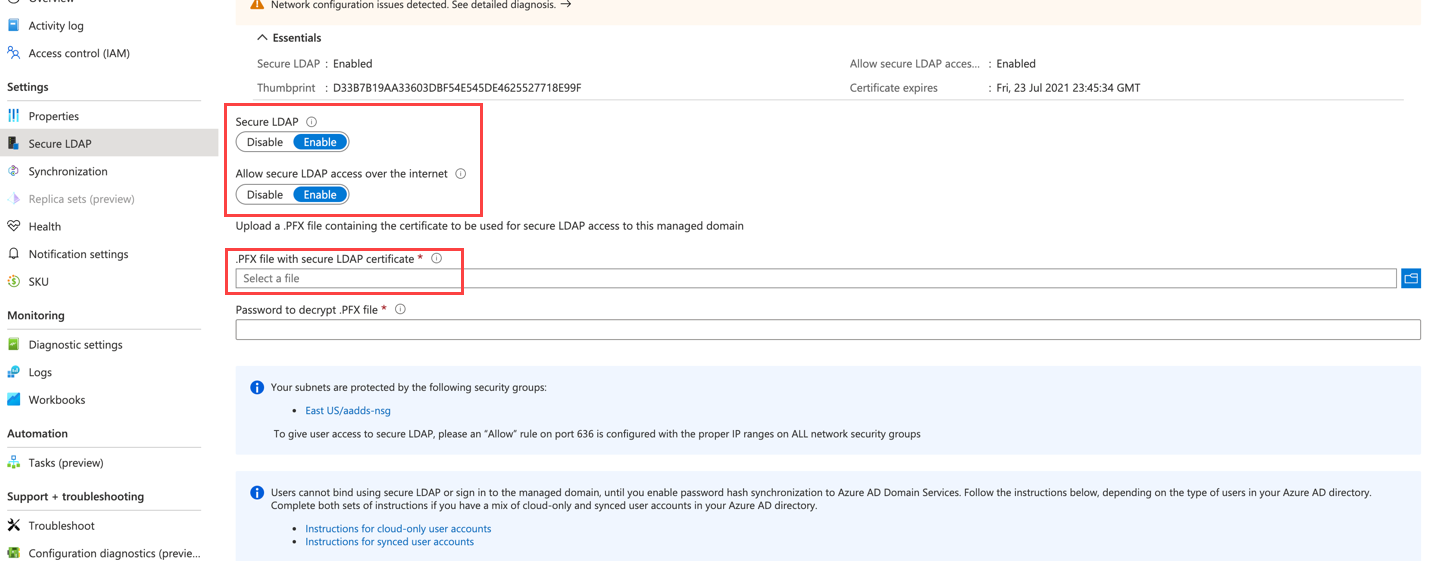
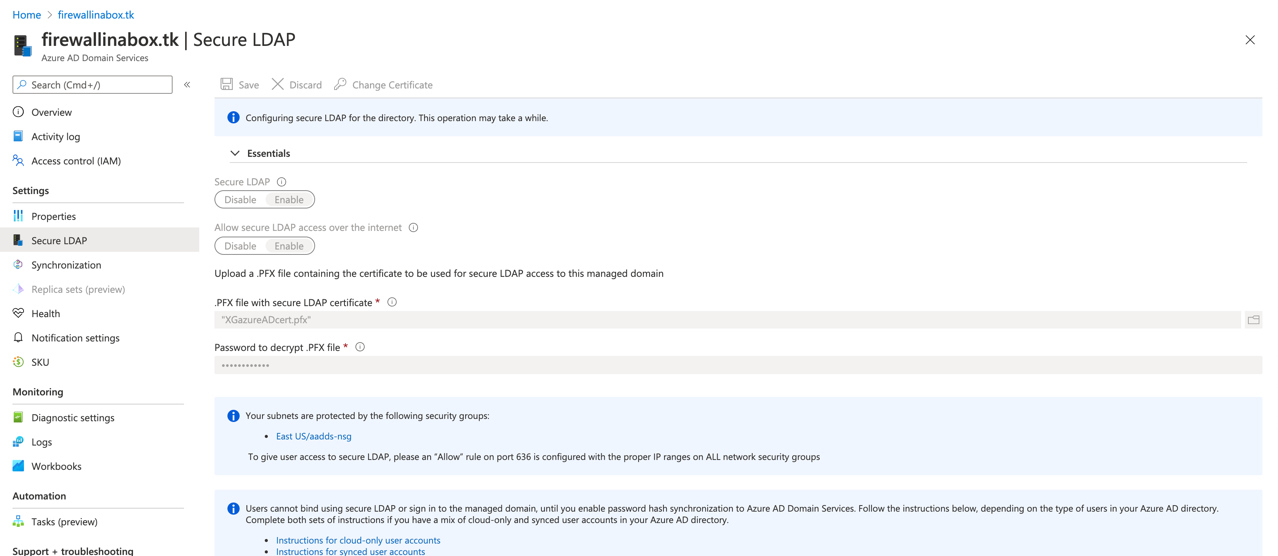
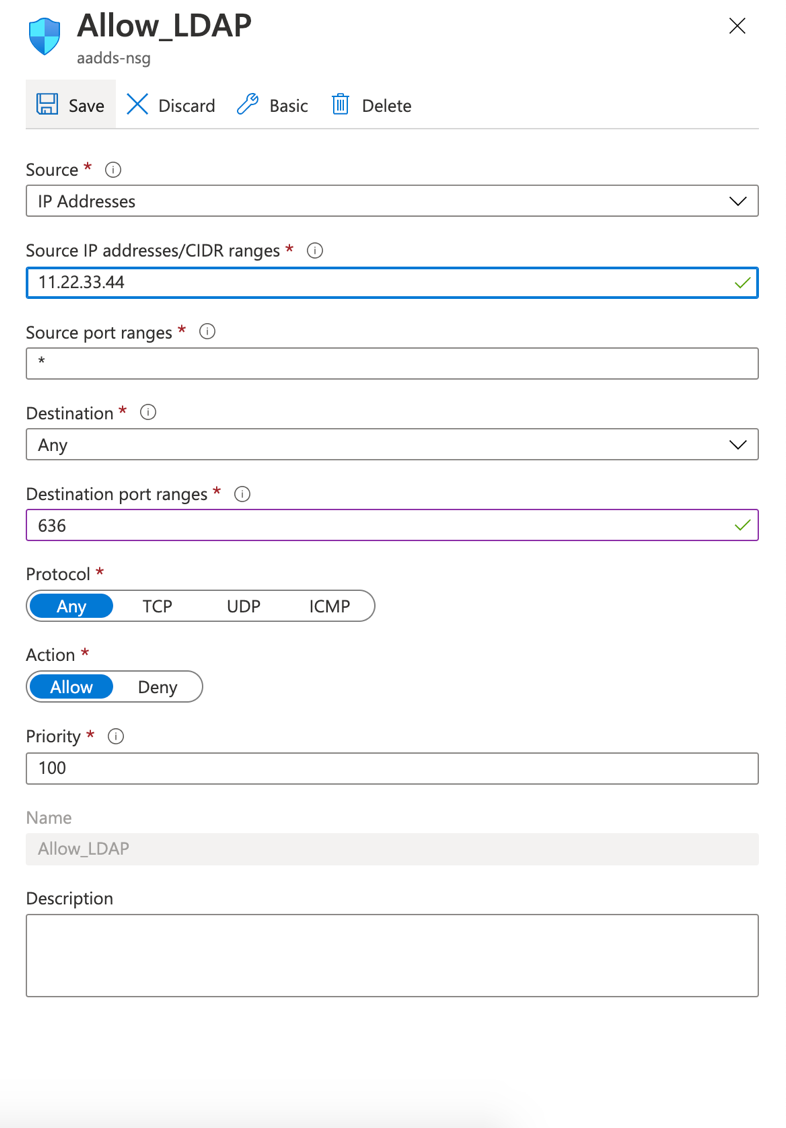
Go to the “tasks” tab and Press “Global settings”, verify that everything is in right place (Can also be done later on individually on the task!):

Press “Save” if you changed anything, and select “Add task”:

We will go for “Single source and destination” migration in this example:

Enter source share:

Add destination SharePoint site:

Give it a name and press “Run now”:

The task is now in “Queued” state:
On the server, after some minutes, you will see the process “MigrationHost” using ressources it will eventually use 90-100%:

When you click the task in the SharePoint migration site, you can see how things are moving on:

And we can see the file server pushing data to the cloud:

Things are in progress, all we need now is to wait 

And we are done:

Go ahead and delete the task and remove the agent from the server, enjoy your data in SharePoint 
Some good FAQ’s: https://docs.microsoft.com/en-us/sharepointmigration/mm-faqs
Souce: https://docs.microsoft.com/en-us/sharepointmigration/mm-get-started



























 !!
!!